If we look at how the coronavirus pandemic has impacted the trends in cybersecurity, we can notice the number of cyber-attacks sharply exceeded the norms. Since individuals working from home do not have the same level of protection or vigilance, cyber-attackers recognized an opportunity to exploit these new cybersecurity vulnerabilities. In this article, we will focus on the main features of the ServiceNow Quebec release for Security Incident Response and Vulnerability Response modules that can help you to face new threats.

Image 1: Working from home has resulted in more phishing attacks. Quote source: Tessian.
Keep up with the rising volume of phishing attacks
ServiceNow is answering the increasing number of phishing attacks in its Quebec release by additional support for security automation by introducing Predictive Intelligence for user-reported phishing.
Prevent threats from compromising your business, data, and employees
To help SecOps teams to predict the attacker’s strategies and fight them more effectively ServiceNow integrated the MITRE ATT&CK Framework, which is now also available for your instances.
Other major improvements contain CrowdStrike Falcon Sandbox integration and machine learning techniques for vulnerability assignments. We will also summarise the new updates for third-party tools to illustrate the ongoing effort to support the philosophy of a mature centralized system to manage everything under one roof.
Security Incident Response
Major new development
MITRE ATT&CK Framework Support
How did the attacker get in? How are they moving around?
MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) is a globally accessible knowledge base of cyberattack tactics and techniques based on real-world observations.
This new capability maps your security incidents to MITRE ATT&CK to give you an advanced context on the attack.
As Katie Nickels, ATT&CK Threat Intelligence Lead for MITRE says,
‘The sheer volume of reporting and new threat groups threatens to drown overwhelmed analysts. It takes analysts years to build up expertise on a threat group, and new analysts may find it difficult to quickly get up to speed.’
By addressing the above-mentioned issues MITRE ATT&CK helps analysts to better understand and faster classify cyber-attacks and strategies, while security managers are able to discover the holes in security defense.
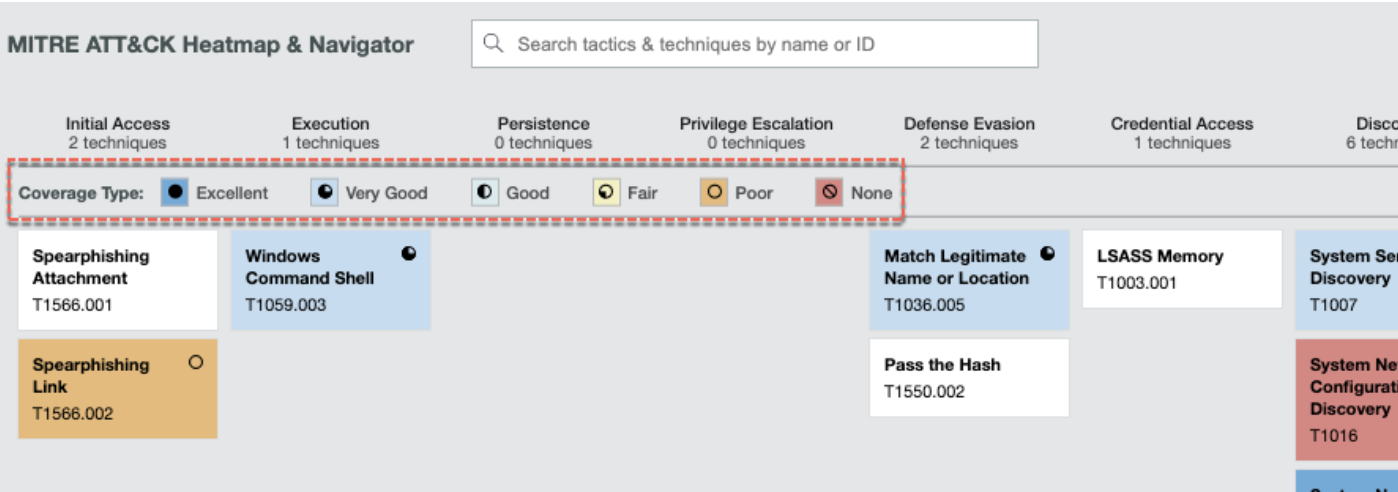
Image 2: MITRE ATT&CK Heatmap and navigator. Image source: MITRE ATT&CK.
Predictive Intelligence for user-reported phishing
The significant solution in triaging and prioritizing
In cybersecurity, the most important factor is time. It is crucial to identify threats as soon as possible. This can be hard with a high volume of phishing incidents coming into the system.
Fortunately, ServiceNow is smart enough to learn and do some prioritization for us.

Image 3: More automation to decrease human error. Quote source: Varonis.
The key is to set up patterns from historical data using machine learning capabilities. These are helping to predict if user-reported phishing emails are truly malicious or not. This feature can support analysts during the analysis phase.
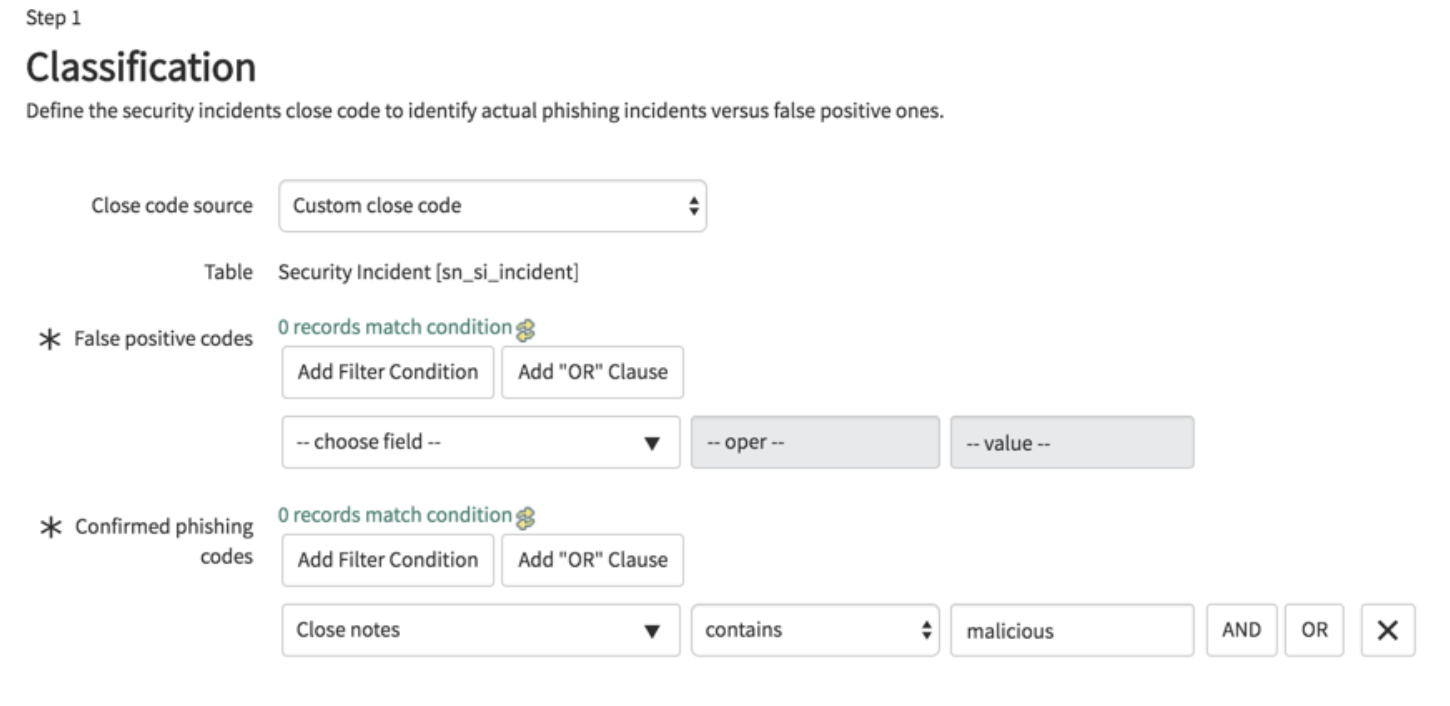
Image 4: Predictive Intelligence for User Reported Phishing. Image source: ServiceNow.
Did you know?
- After declining in 2019, phishing increased in 2020 to account for 1 in every 4,200 emails. (Symantec)
- 65% of groups used spear-phishing as the primary infection vector. (Symantec)
- 1 in 13 web requests leads to malware. (Symantec)
- Phishing attacks account for more than 80% of reported security incidents. (CSO Online)
- $17,700 is lost every minute due to a phishing attack. (CSO Online)
CrowdStrike Falcon Sandbox Integration
Streamline Ingestion of Observables
Have you ever wondered how to deal with suspicious but not solidly malicious observables?
Safe forensics on a virtual machine
Analysts can determine whether the file is malicious without leaving the ServiceNow platform and an open incident with direct integration of CrowdStrike Falcon Sandbox.
Automatically submit observables from security incidents to CrowdStrike Falcon Sandbox saving security analysts time and effort.
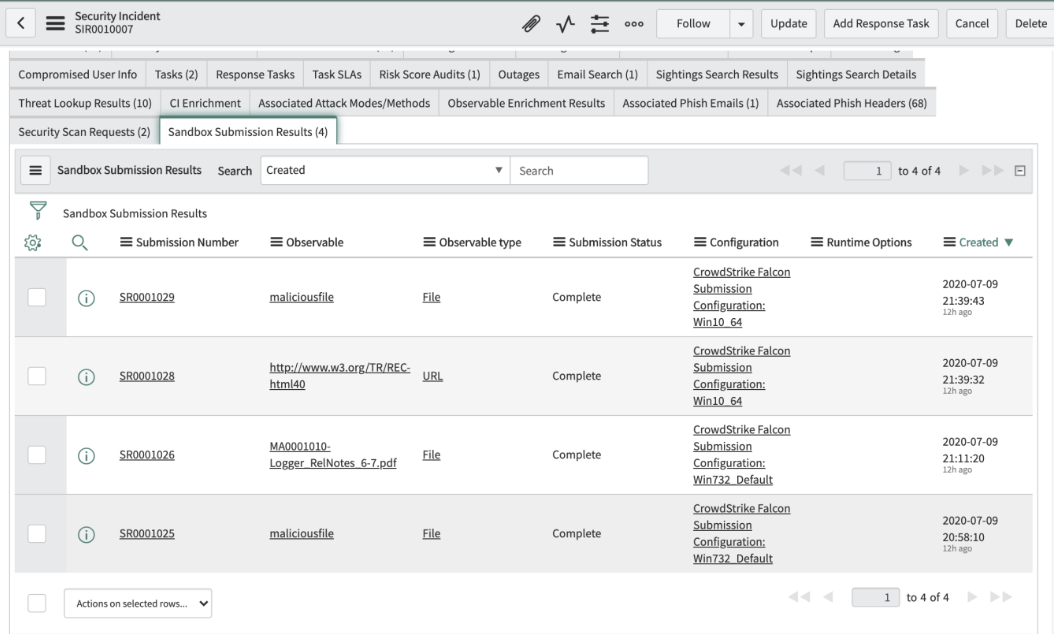
Image 5: Crowdstrike Falcon Sandbox Integration – Sandbox Submission Results. Image source: ServiceNow.

Did you know?
- 48% of malicious email attachments are office files. (Symantec)
- 94% of malware is delivered by email. (CSO Online)
- The average cost of a ransomware attack on businesses is $133,000. (SafeAtLast)
- Most malicious domains, about 60%, are associated with spam campaigns. (Cisco)
- About 20% of malicious domains are very new and used around one week after they are registered. (Cisco)
Other enhancements
Secureworks CTP Integration (MSSP)
Secureworks Incident Updates and Resolution. Automated incident creation from Secureworks incidents/ tickets and allows the MSSP to ingest incidents from Secureworks and automate the process in SIR.
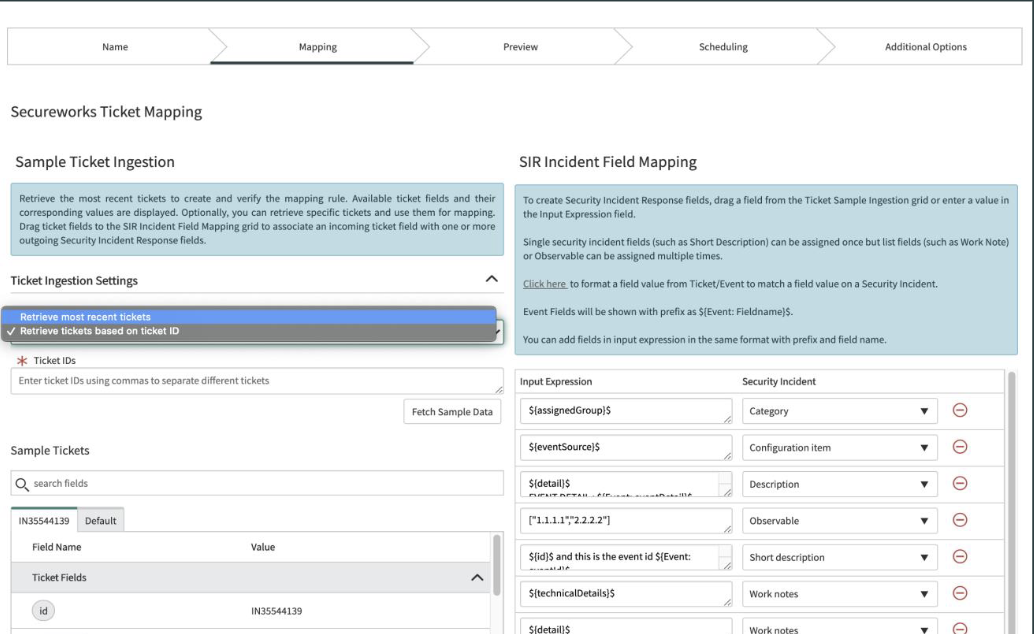
Image 6: Secureworks CTP Integration (MSSP). Image source: ServiceNow.
Updated TAXII support
TAXII (Trusted Automated Exchange of Intelligence Information)
To access a broader array of Threat Intelligence. Threat Intelligence is supporting TAXII 2.0 and TAXII 2.1. Threat sources supporting these protocols are available.
Further Integration Updates
Following integrations were implemented or updated since the Paris release:

Vulnerability Response
Major new development
Vulnerability Assignment Recommendations
Leverage Machine Learning to Identify Owners
Benefit from machine learning to find the most appropriate team for various collections of vulnerability items.
Application Vulnerability Management
Gain Actionable Insights into Application Vulnerabilities
Application vulnerability scanners are trying to discover the vulnerabilities on custom pieces of software such as corporate applications which are facing the web. Vulnerability Response capability that integrates with Veracode to scan for DAST (Dynamic App Security Testing).

Image 6: Do you know the number of high-risk vulnerabilities on your company network?. Quote source: Positive Technologies.
Chief Information Security Officer (CISO) dashboard in Performance Analytics (v 13.0)
To better understand the trends and make data-based decisions
A new dashboard was introduced to give an insight into how effective your current Vulnerability Response setup is. CISO can see the scan coverage and current trends so that the requiring more attention can be identified more easily. The real nice part is the Recommended Actions tab containing useful tips to resolve rising issues.
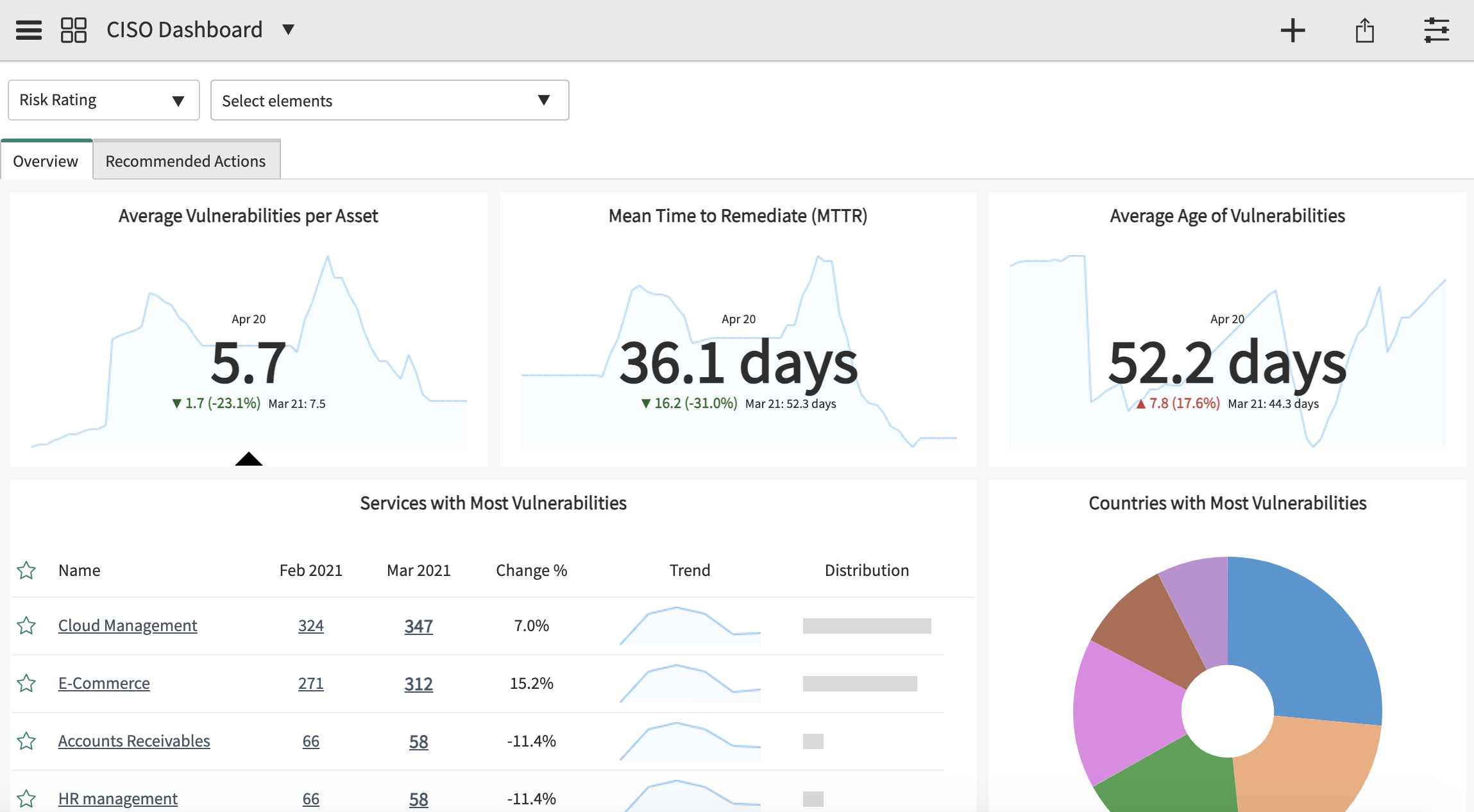
Image 7: Vulnerability Response – CISO Dashboard. Image source: ServiceNow.

Did you know?
- Frequent scanning correlates to much faster remediation time (Veracode)
- Unpatched vulnerabilities were involved in 60% of data breaches (Ponemon)
- Half of all vulnerabilities remain unfixed six months after discovery (Veracode)
- 84% of companies have high-risk vulnerabilities on their network perimeter (Veracode)
- Microsoft had 150% more vulnerabilities disclosed in Q2 2020 than all of 2019 (Risk-based security)
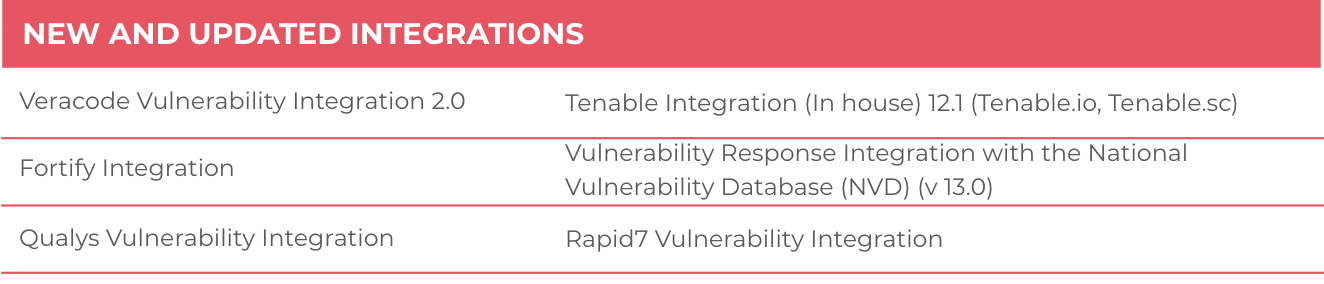
Further Integration Updates
Following integrations were implemented or updated since the Paris release:
Upgrade to Quebec today
ServiceNow is constantly evolving and serving new functionalities to keep up with big-picture trends and strategies. This applies specifically for Security Incident Response and Vulnerability Response, which are changing very dynamically having new functionality store releases on a monthly basis.
Disclaimer: Information and screenshots used in this article are coming from official ServiceNow documentation released for the Quebec upgrade and official documentation of the integrated third-party tools.
Do you have any questions? Don’t hesitate to contact us!
