Managing cyber security risks remains an uphill battle. Threats keep growing in numbers, as well as sophistication, and most cyber security departments are already overloaded.
3 main challenges
Increasing compliance requirements and external threats
Shortage of skilled cyber security professionals
An opaque and ever-changing IT infrastructure
Compliance demands drain security resources

Obviously, it makes good sense to comply with requirements issued by various authorities. Still, if you look at it from an organization’s security point of view, spending too much time gathering evidence to report on compliance, actually weakens the effort to protect the organization from emerging threats.
Sure, the measures required by the regulations are often reasonable but compliance also requires an immense amount of effort for documentation and reporting. The organization is often requested to provide information that very soon becomes obsolete due to the ever-changing situation. That is “pseudo-security”, draining the organization’s security resources while it does not increase the level of protection. This can be done smarter.
Chronic lack of skilled workers seriously depletes security measures
According to the 2021 Cybersecurity Workforce Study from the (ISC)2, the size of the global cybersecurity workforce is 65% below what it needs to be, and there is no prospect of significant improvement. This considerable deficit in the staff impacts the organization’s effort to maintain an acceptable level of security. Because of this lack of cyber professionals, we have to work smarter. Do more quality work with fewer hands.
Insufficient insight into IT systems makes them hard to defend
You can only protect what you know, but security managers usually do not have an updated and complete rundown of the IT landscape. It is a complex set of systems located in separate interconnected entities. Moreover, the IT infrastructure and IT applications change constantly, requiring regular updates. So, how many people need to be involved to predict and assess upcoming risks in a constantly changing business and IT environment? Risk management becomes a very difficult task if it is to be performed manually and nearly impossible to maintain afterward.
These profound challenges are not just a problem for the specific organization; they are a societal threat. Cybersecurity is the frontline of the 21st century, and if organizations cannot defend themselves, much more is at stake: Our economy, democracy, and our way of life.
Three ways to free security resources
What is the way forward?
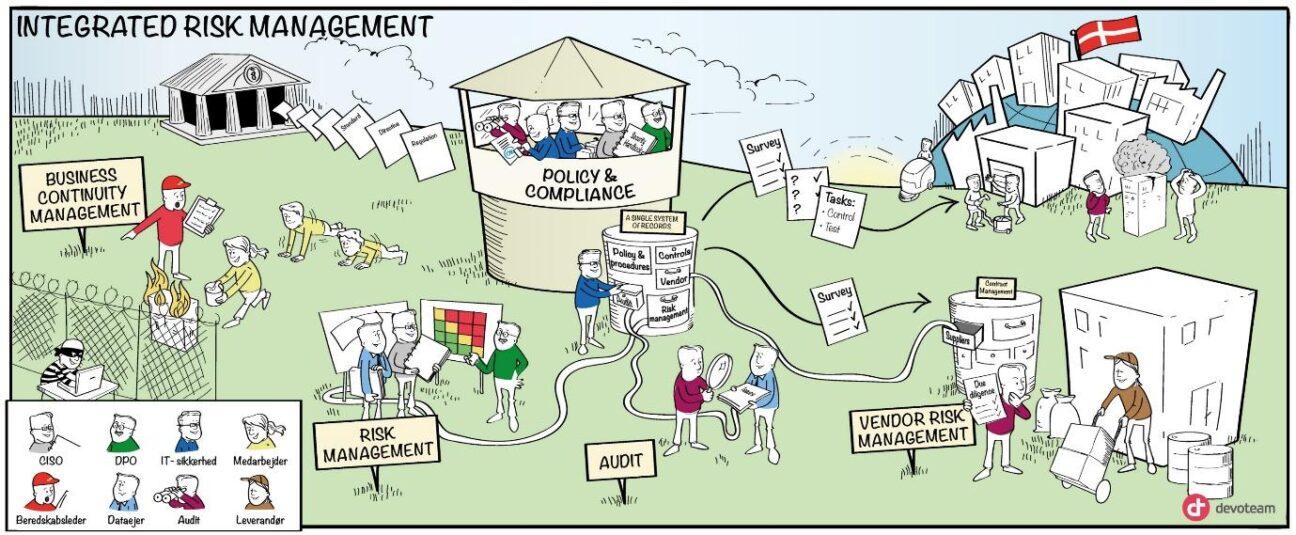
The common denominators for the above challenges are a deficit of resources and reliable data. To reduce these deficits substantially, we suggest working smarter and enabling technology to free up time to work with essential protection. Such an approach does not require large investments in technology or programs. Most organizations already have the necessary technology tools to improve their situation. Enterprise Service Management (ESM) platforms, like ServiceNow®, are traditionally used to manage IT services in the organization. Today, ServiceNow is an automated workflow platform that is able to collect and connect data, control workflows and deliver real-time reporting. Therefore, ServiceNow is the ideal platform to orchestrate and automate your security and compliance processes. It allows you to free up time for your security professionals, so they can focus on protection, detection, and response. How would that work? With automation, crowdsourcing, and system utilization.
Automation
The primary reason why evidence collection and documentation for compliance purposes are such a drain on resources is that most of the work is done manually. But usually, most of the information is already accessible from the IT systems, so why not create automatic processes to collect the data and present the results?
You need to remember that the compliance process is mostly repeatable and predictable actions and therefore easy to automate, especially with ServiceNow. That way you avoid disturbing your business users by asking unnecessary questions you already can retrieve the answers to.
Crowdsourcing
For a central Governance, Risk and Compliance (GRC) function with limited resources, it is highly challenging to protect the organization appropriately. But GRC can expand its resources through crowdsourcing so that the protection becomes an actionable issue for the entire organization. Crowdsourcing would work by allocating relatively small tasks to a rather large amount of people. That way, you are taking advantage of the knowledge and skills from people who are part of the business process or users of IT systems and have firsthand knowledge.
The tasks must be:
- limited,
- precise,
- targeted at specific job functions and roles in the organization.
With ServiceNow, you can design processes where you collect pieces of information across the organization while keeping a clear outline of the tasks submitted.
System utilization
You can also let the systems do some of the work. ServiceNow makes it possible to get a holistic, constantly updated overview of all IT systems running. You can measure the data according to various parameters, for example, dependencies or business criticality. That way IT systems can be set to a specific security baseline, depending on their criticality and nonconformities, and can be automatically reported.
Do more with the same
Lack of skilled security professionals and constantly new security threats. These two things are not going to change anytime soon. Therefore, the organization must do more, with the same security professionals, if they aim to keep up the pace.
By applying the three approaches above, the organization will free up time for their valuable resources to do work that genuinely improves the organization’s security and business. And you get a clear, dynamic outline of the IT infrastructure where ServiceNow provides reliable updated data.
If you want to know more about how to apply your resources and strengthen security, contact: frederik.helweg-larsen@devoteam.com or Jorgen.papadopoulos@devoteam.com
Would you like to know more? Watch our on-demand webinar”Automate your cyber security with ServiceNow“!
Devoteam: Tech and people to secure the future
We believe that cybersecurity and technology are mutually dependent. That is why Devoteam has wide-ranging expertise and experience with solid human values in both areas. We help you understand the business landscape and swiftly address risks to obtain ultimate security. And we shape innovative digital businesses with intelligent solutions and optimized processes for people.
